According to Deraison & Gula (2009) detecting wireless access points is a major source of activity for many enterprise security groups and they suggest manual inspection and dedicated system audits as two methods that can be used for this task.
Manual audits
Conducting a system audit with a wireless enabled notebook computer or a PDA device and walking around the network premises will help locate any access points connected and transmitting wireless signals. This would require physical access to all locations of the network. Utilizing RF scanning systems would assist in pin pointing the access point locations much easily.
Dedicated auditing can use some of the techniques as below.
Centralized monitoring
There are solutions available that can utilize authorized access points of the company network to transmit any other wireless signals they detect to a centralized consol. Jim Geier (2003) identifies Air Wave as an example. By examining this data would help to identify any unauthorized connections from a central point and this method suits any large network.
Port scanning
Employing software tools to do a TCP port scan of the company network would list all devices with port 80 enabled. Port 80 is associated with HTTP protocol network traffic and Geier (2003) points this technique will detect web servers, printers and nearly all access points. This method would also suit large networks.
Nessus vulnerability scanner is an example of software that performs port scanning.
Once the access points are identified, further checks will be required to determine if the access point is really a rogue access point.
Check if default SSID is used
Check if SSID is set to broadcast
Check if default administrator account is accessible using default password
Check if MAC address filtering is used
Vendor name, device type, model
Security configuration
Check if encryption is used
Finding items in the above list with default values in use or no values set are indicators the access point is a rogue one according to Peláez (2004).
References
Deraison, R, Gula, R, 2009, Using nessus to detect wireless access points,
http://www.nessus.org/whitepapers/wap-id-nessus.pdf
Geier, J, 2003, Identifying rogue access points,
http://www.wi-fiplanet.com/tutorials/article.php/1564431/Identifying-Rogue-Access-Points.htm
¬Peláez, R, 2004, Auditing 802.11 wireless networks focusing on the Linksys BEFW11S4
Access Point, An auditors perspective, http://it-audit.sans.org/community/papers/auditing-80211-wireless-networks-focusing-linksys-befw11s4-access-point_121
Pacchiano, R, 2006, How to Track Down Rogue Wireless Access Points,
http://www.smallbusinesscomputing.com/webmaster/article.php/3590656/How-to-Track-Down-Rogue-Wireless-Access-Points.htm
Wednesday, September 22, 2010
Monday, September 20, 2010
Vulnerability assessment - Nessus Vulnerability Scanner
Download Nessus vulnerability scanner
Fill requested information and submit.
Start server
Use default values and obtain activation code.Start client
This step could not be performed successfully due to below error.Wireless security - Spoof a MAC address using SMAC
Download SMAC from www.klcconsulting.net/smac
SMAC 2.0 allows (Media Access Control) MAC address to be changed for a network adaptor or otherwise known as spoofing the MAC address.This task demonstrates how to exploit a vulnerability that is present in wireless networks. An attacker could find out a valid MAC address allowed by an access point, spoof the attackers network adapter to use the allowed MAC address and connect to the network.
Install and run application
View the MAC address
Update to a new MAC address
The evaluation copy allows 0C-0C-0C-0C-0C-0C to be updated. The program also had to be run as administrator for Windows Vista version.Start a command prompt
View the adapter information
Type ipconfig/all and enter. The updated MAC is displayed.Thursday, September 16, 2010
Cryptography - Hash generators & comparing hashes
Hash
One of the basic algorithms of cryptography is the hashing algorithm. Given an original block of message the algorithm will generate a hash that is unique for this particular message.Advantage of a hash is that it is not feasible to compute the original message by reverse calculating the hash.
A common use of a hash is to check the integrity of a message. As an example ATMs use the hashed password stored on the card and the entered password hashed to validate the user.
MD5Deep
This is a set of programs to compute various hash keys for a given input file or files.Create the input message
Create a word file with the text "Now is the time for all good men to come to the aid of their country".Save the file
Create a hash
Execute md5deep and provide the above file name as it's input.md5deep g:\csinfo\itc358\assessment2\country.docx
The generated hash key will be displayed. The length of the hash created is 128 bits or 16 bytes. The value shown is in 32 hexadecimal characters.
Create a hash
Use the md5deep documentation file as input to create another hash.The length of the hash created is 128 bits or 16 bytes. The value shown is in 32 hexadecimal characters. This conforms to the requirement of a good hash algorithm to generate a consistent hash value regardless of the content length used to generate the hash.
Modify the message contents
Open the word file created as input to hash 1 and modify it by removing the fullstop at the end of the sentence.Create a hash using the modified word file
Even the slightest modification has resulted in creating a completely new has value.This proves the hash function can be used to check the integrity of a message.
Create a hash using sha1deep
The hash value length is 160 bits or 20 bytes long for both documents but the hash value is significantly different for the two documents.Create a hash using sha256deep
The hash value length is 256 bits long for both documents but the hash value is significantly different for the two documents.Create a hash using whirlpooldeep
The hash value length is 512 bits long for both documents but the hash value is significantly different for the two documents. The displayed hash value is in 128 hexadecimal digits.Wednesday, September 1, 2010
Cryptography - Uses for hashes
Hash
Creating a hash value is a basic function of cryptography. The input is processed by a hashing function and the output is the hash value or message digest. Ciampa (2009) describes a hashing algorithm as the most basic cryptographic algorithm. A characteristic of a good hashing function is that no two different messages will produce the same hash value and the hash value cannot be reversed in order to find the original message. Additionally regardless of the input message length the output hash value length will be a fixed number of characters.Standard Hash Algorithms
MD5 – Message digest algorithm version 5SHA – Secure hashing algorithm
Whirlpool - Whirlpool hashing algothirm
Uses of hashes
Client authentication by a server is a good scenario for using hash values. As an example Ciampa (2009) describes how ATMs use hash values to validate user’s entered password hashed against the hashed password stored on the card.
This avoids the need to transmit passwords over the network, more efficient, more secure.
A message can be verified as the original with the use of a hash value.
The creator of the message generates a hash value also known as a message digest. The recipient can generate the hash value and compare with the original hash to verify the message content is original and has not been modified. However this technique does not provide confidentiality of the message.
Stallings(2005)describes three alternative ways in which the above technique can be used to obtain authenticity as well as confidentiality.
- Using conventional encryption
- Using public-key encryption
- Using secret value
Another use of hash function is message integrity check which is a digital signature found in secure email according to Pfleeger and Pfleeger (2007)
References
Ciampa, M, 2009, Security+ guide to network security fundamentals,Pfleeger, C, Pfleeger, S, 2007, Security in computing, Prentice hall
Stallings, W, 2005, Business data communications, Prentice hall
Labels:
Assessment 2
Saturday, August 21, 2010
Wireshark - Protocol Analyser
Networks
Computer networks have become an important part of our daily life. We rely and depend on such networks to accomplish many tasks on a daily basis we often do not realize their existence. The phone calls, paying bills, transport, operating of rail and road networks everything depend on the computer networks that provide and carry out many tasks electronically.Therefore networks attract significant attention when it comes to security and the number of attacks being carried out on them are increasing.
Vulnerabilities
Variety of devices, protocols, transmission, data and applications that make up thenetwork contributes to the many vulnerabilities the network will possess.
Attacks
Denial of service, spoofing, man-in-the-middle and replay are some of the types of attacks that can be performed on a network.Wireshark
Wireshark is worlds foremost network protocol analyser according to their about wireshark Webpage.This tool can be used on many different platforms to analyse a variety of protocols that a device is receiving and transmitting.
The windows installation is utilizing another industry standard software called WinPcap, Windows packet capture library. This is used to gain link layer network access on Windows environments.
Download Wireshark
Wireshark can be downloaded from the website download page or one of the mirror sites listed on their website. Once the download is complete run the .exe to install the software. It will prompt to install WinPcap and use the default setting of start WinPcap on start up to enable easy use of the application.Launch Wireshark
Launch Wireshark and click Capture and Interfaces. Select the network interface adapter of the computer and click start button.View captured packets
Depending on the network traffic, it will capture and display the packets captured.If nothing appears untick "capture packets in promiscuous mode".
View login information
Direct the web browser to url www.medialightbox.com/loginEnter user id Gerald and password happy and press enter. The login attempt will fail as there is no valid user with this credentials and an error message will be displayed as below.
Find data in packets
Return to Wireshark window, click edit then find packet. Click string, type Gerald in the filter field and click find. Records will be shown which contains the searched string.In steps 7 and 8 the wireshark captures the data being transmitted to and from the computer as data packets. Their contents are then displayed along with other information such as source, destination IP address, protocol and status codes.
When the data are transmitted as encrypted content such using ssl protocol wireshark will not be able to display the data content as plain text.
Saturday, July 24, 2010
Question 3 – Virus attacks
Computer security
Security in the context of computers mean addressing the important aspects of Confidentiality, Integrity and Availability of the computer system.A good secure system would have achieved the right balance of these three aspects in relation to data, software and hardware of the particular computer system. Once a system is secured it has a lower possibility of being subject to be exploited the vulnerabilities of the system.
Virus
Computer viruses are software that can cause damage to the computer system that it resides in as well as spread itself (the software) to other computer systems. These viruses have the ability to attach them selves to another object such as a document or file and once the document or file is opened or executed by the user, virus will spread to that computer system. If this file were copied to another the virus would spread the same way to that computer. This processes will enable viruses to spread and infect many computer systems. Today's highly networked systems and the Internet has enabled an ideal medium for the viruses to spread.Viruses exploit vulnerabilities that exist in software and destroy, alter or compromise data on a computer system.
Worst computer viruses
While there may be many different ways to categorize a computer virus such as, the damage caused, the hardness to detect, the time taken to spread and so on code red, Melissa, I love you & nimda can be listed as well known and worst effecting viruses that have spread in the computing world so far.Based on an article by (Thorsberg, 2002) worlds worst viruses are
- LoveLetter - I love you virus (2000)
- Klez worm (Oct 2001)
- Melissa virus (Mar 2001)
- Magistr (Mar 2001)
- Explorer.zip worm (1999)
- Anna Kournikova (or VBS.SST@mm) worm (Feb 2001)
- Nimda virus (Sep 2001)
- Benjamin worm (May 2002)
- Code red worm(2001)
- Sircam (Jul 2001)
The latest viruses
Examining Symantec's security response page (Symantec, 2010a) few of the latest threats are listed below and the vulnerabilities were noted on Microsoft Windows, Microsoft Access, Outlook, Adobe flash player and Adobe reader.- W32.Changeup.C - Worm
- This was discovered on 23 july 2010 and infected Windows 95, Windows 98, Windows XP, Windows Me, Windows Vista, Windows NT, Windows server 2003 and Windows 2000 systems. The worm exploits a vulnerability in Microsoft Windows shortcut 'LNK' files automatic file execution and spread through removable and shared drives.
- Bloodhound.Exploit.343 - Trojan, Virus, Worm
- Symantec lists Windows systems as affected by this worm and it also exploits the Microsoft Windows shortcut 'LNK' files automatic file execution vulnerability.
- Bloodhound.Exploit.341 - Trojan, Virus, Worm
- Windows systems are affected by this worm and it exploits a Microsoft Outlook TNEF Stream with MAPI attachment Remote code execution vulnerability according to Symantec.
(McAfee, 2010b) had the below list of malware on it's threat center web page on the same day and noted Microsoft Windows, Microsoft Office and Internet Explorer on the current vulnerabilities list.
- Exploit-CVE2010-2568
- (McAfee, 2010a) described this malware as exploiting a vulnerability found in Microsoft windows shell code which allows code execution via a maliciously crafted .lnk file. Removable USB drives and shared folders were noted means of spreading for this malware.
- MSIL/Terdial.d
- This particular malware periodically dials premium rate/high cost long distance phone numbers according to (McAfee, 2010b) MSIL/Terdial.D description. It requires compact .NET framework installed to run the malicious code and is packaged with a legitimate game called “PDA Poker Art” according to Mcafee’s description.
The latest attacks
According to the Internet security threat report by (Symantec, 2010b) Hydraq trojan was used to carry out attacks on large companies in January 2010. This trojan has used a previous unknown vulnerability in Microsoft Internet Explorer and a patched vulnerability in Adobe Reader and Adobe Flash. Attackers have been able to gain full remote access to the computers once the Trojan has been installed.Further according to the same report in 2009 a major attack has been carried out against a single credit card payment processor, hacking in to the network using an SQL-injection attack.
Crimeware kits
An increasing problem with computer attacks would be the crimeware kits, a toolkit that allows people to customize malicious code and includes a variety of different exploits. Some examples of these are Zeus kit which could be bought for $700 or even free from underground forums. Fragus, Eleonore and Neosploit are also well known attack kits that can be used for web attacks according to (Symantec, 2010b)References
McAfee (2010a). Exploit-CVE2010-2568 Retrieved 31/07/2010, from
http://vil.nai.com/vil/Content/v_268562.htm
McAfee (2010b). MSIL/Terdial.D Retrieved 31/07/2010, from
http://vil.nai.com/vil/Content/v_268519.htm
Symantec (2010a). Security response Retrieved 23/07/2010, from
http://www.symantec.com/business/security_response/landing/threats.jsp
Symantec (2010b). Symantec global internet security threat report. Trends for 2009, XV.
Retrieved from http://eval.symantec.com/mktginfo/enterprise/white_papers/b-whitepaper_internet_security_threat_report_xv_04-2010.en-us.pdf
Thorsberg, F. (2002). The world's worst viruses, from
http://www.pcworld.com/article/103992/the_worlds_worst_viruses.html
Friday, July 23, 2010
Question 2 – Keylogger
A key logger could be in the form of software or hardware and it collects and records all key strokes that are typed. The recorded information could be used by a computer attacker to gain access to information or the computer system.
The collected information will then be emailed to a pre programmed email id. Also these programs does not run as applications on the installed computer and is difficult to detect.
Due to the small size and the fact the key board is connected at the back of the computer these are also very difficult to detect once installed.
Keystorke Recorder & www.softdd.com
or
Keystorke Recorder & www.cnet.com
Below screen is displayed if you follow link 1.
Software keylogger
A software key logger could be installed via a computer virus or a Trojan.The collected information will then be emailed to a pre programmed email id. Also these programs does not run as applications on the installed computer and is difficult to detect.
Hardware keylogger
A hardware component that could be inserted between the key board connector cable and the computer keyboard port. The attacker must have physical access to the computer to install and remove the device once the information is captured.Due to the small size and the fact the key board is connected at the back of the computer these are also very difficult to detect once installed.
Installing a keylogger software
Below steps demonstrate how to install a software key logger on a computer and how the data will be captured once it is in operation.Step 1 - Download key logger
The particular keylogger used for this task is Keyboard Collector and can be downloaded fromKeystorke Recorder & www.softdd.com
or
Keystorke Recorder & www.cnet.com
Below screen is displayed if you follow link 1.
Step 2 - Install & run key logger
If the computer is installed with anti virus software it may be required to stop it for the duration of the below tasks or modify settings to allow the keylogger software to be downloaded and installed. Download and install the keylogger software. Once download is complete click the .exe file to install.Step 3 - View recorded log
Once the software is running perform normal computer activities. I opened a notepad file and typed in some text. Then click on keyboard collector icon to execute it and click on view logs. Below screen shows it has captured the text I typed into the notepad file.Step 3 - Detect keyboard collector
The keylogger software is designed to run undetected on the installed computers. On a windows computer click task manager, then applications and keyboard collector will not appear to be running in the applications as shown below.Additional step - Detect keyboard collector
Examining the running processes kcol23.exe was found as shown below.Uninstall keyboard collector
Uninstall using the uninstall provided on the keyboard collector software. However this did not appear to remove all the components and the directory where it was installed and the kcol23.exe still remained. They required to be deleted manually and activate the antivirus software if it was stopped.Saturday, July 17, 2010
Question 4 – Anti virus software
A computer system could be strengthened by installing an antivirus software which will scan a computer for security risks, clean or remove viruses found, keeps the virus definitions updated automatically by synchronising with the antivirus software server and provides a variety of additional functions such as firewall functionality, web site security certificate verification, computer configuration and back up functionality.
This task is designed to test a variety of means that a computer could be effected with a virus file and how the antivirus software installed on the computer will detect and secure the computer. The tasks performed below is to download a fake virus file and observe how the installed antivirus software will detect and prevent each different scenario.
This task is designed to test a variety of means that a computer could be effected with a virus file and how the antivirus software installed on the computer will detect and secure the computer. The tasks performed below is to download a fake virus file and observe how the installed antivirus software will detect and prevent each different scenario.
Step 1 - The test virus file
Below screen shows the antivirus test file download page from European Institute for Computer Antivirus Research website.Step 2 - Risk via URL
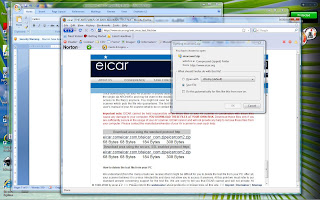
Below screen shows when the link to eicar.com is clicked the antivirus software displays a pop up window stating a security risk was blocked and the computer is secure.Step 3 - Risk via downloading a compressed file
When the eicar_com.zip file link was clicked the dialog box opened, with default setting of “save file” selected. But no alert from antivirus software was displayed.Once the download is complete, the file was selected and a virus scan was performed.
Antivirus software detected and reported a virus was found.
Step 4 - Risk via a double compressed file
Next task is to download a double compressed zip file called as eicarcom2.zip. The file could be saved to the computer with no warnings.Once the download was complete the file was selected and scanned for viruses using the antivirus software.
A security risk was detected and reported by the antivirus software program.
Question 1 – Google Reconnaissance
Computer attackers are able to gather unprotected information using Google search to attack such computers. This is known as “Google reconnaissance”. The steps below illustrate how the information could be collected for carrying out such an attack.
Uncover MS Excel files with login infomation
Below steps illustrate how a Google search can be performed to retrieve MS Excel files containing user id and password information in clear text. These could then be used to log into or gain access into the computer system or the network.step 1
Use Google advanced search, search words containing “login:*” “password=*”, select file types MS excel “.xls”, then click advanced search.step 2
Below screen shows 1st page of results found by Google that matches the search criteria.step 3
The screen below shows contents of a MS Excel file that contains an actual user id and a password value for a web site with the URL of the web site.Uncover Text files with login infomation
A similar search can be performed to search for text files that contain user id and password values.
step 1
The search criteria is, “index.of passlist” as the search word and any format as the file type.step 2
Below screen displays 1st result page returned by Google.step 3
Examining the results many did not contain an actual file with user id and password values.step 4
A slight modification was done to the search as "index.of password" and click search button. The results returned are shown belowstep 5
Following the first link displayed the contents of a directory index of a site with a list of files and possibly links to a password file as shown below.step 6
Click the link passlist.txt and it provides access to what appears to be a admin user id and password which is unprotected as shown below.Friday, July 9, 2010
About
ICT Management & Information Security is a topic that will be relevant to anyone using information technology today. From corporate IT management to a personal computer user, even someone using a mobile device would benefit from the knowledge of Information security.
This blog will be used to document my study activities on the topic of ICT management and information security.
Information contained in this blog are for educational purposes only. Tasks or activities demonstrated are not carried out to gain access to and carry out any task that will damage, destroy or reveal unauthorised personal or financial information.
Stay tuned.
This blog will be used to document my study activities on the topic of ICT management and information security.
Information contained in this blog are for educational purposes only. Tasks or activities demonstrated are not carried out to gain access to and carry out any task that will damage, destroy or reveal unauthorised personal or financial information.
Stay tuned.
Subscribe to:
Comments (Atom)